159 results found
NRD Cyber Security
CyberSet
CyberSet is a services automation toolkit for CSIRTs or SOCs. It works as a set of technologies and...
Wedos
WGP - Anycast DNS, DDoS protection, CDN
First-class protection against cyberattacks on multiple layers, and ultra-fast website content...
Secfense
Secfense IdP (Identity Provider) | Secure, flexible and simplified identity management
Secfense IdP marks a significant advancement in cybersecurity, delivering unparalleled flexibility...
Sagenso
Telescope
Telescope, is an automated cybersecurity audit tool that evaluates a company's existing security...
Malizen
Malizen
Experience streamlined security data analytics with Malizen, a no-code interface that connects all...
Cryptomage
Cryptomage Cyber Eye
Cryptomage Cyber Eye™ Network Detection and Response-class network probe is much more than a simple...
CyberDesk
Identity-Centric Data Security
CyberDesk helps you to adaptively control who can perform what actions with what data. Covering both...
Threema GmbH
Threema Work. The Secure Business Messenger
Threema Work is a secure and GDPR-compliant business communication solution that facilitates mobile...
Secure Practice
PrepJam by Secure Practice
Change how your company teaches and practices cyber security. Secure Practice blends immersive...
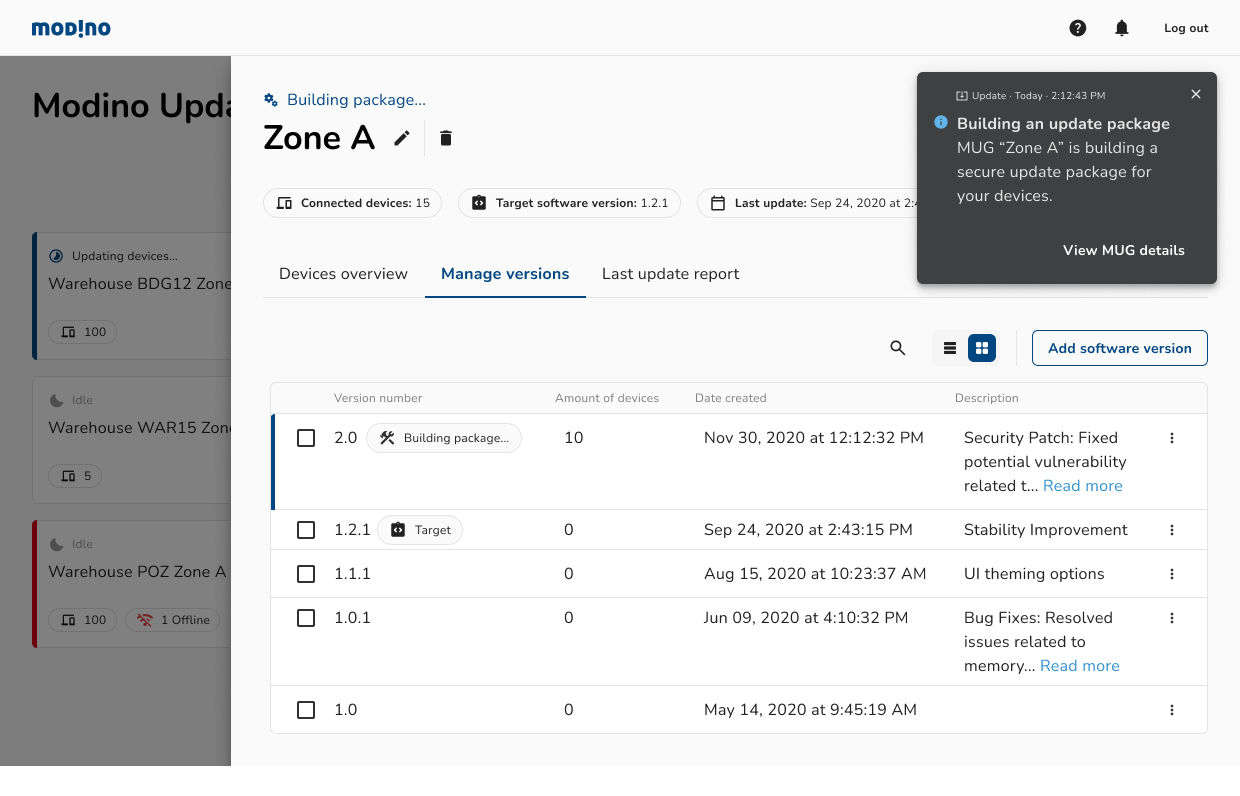
Modino.io
Modino.io - safe and secure digital artifacts delivery
Modino.io is an on-prem / cloud platform for performing safe and secure updates for: - IoT devices -...
Binalyze
Binalyze AIR
Binalyze AIR is an investigation and response automation platform powered by forensic-level...