Binalyze AIR
Binalyze AIR is an investigation and response automation platform powered by forensic-level...
Threema Work. The Secure Business Messenger
Threema Work is a secure and GDPR-compliant business communication solution that facilitates mobile...
WALLIX PAM
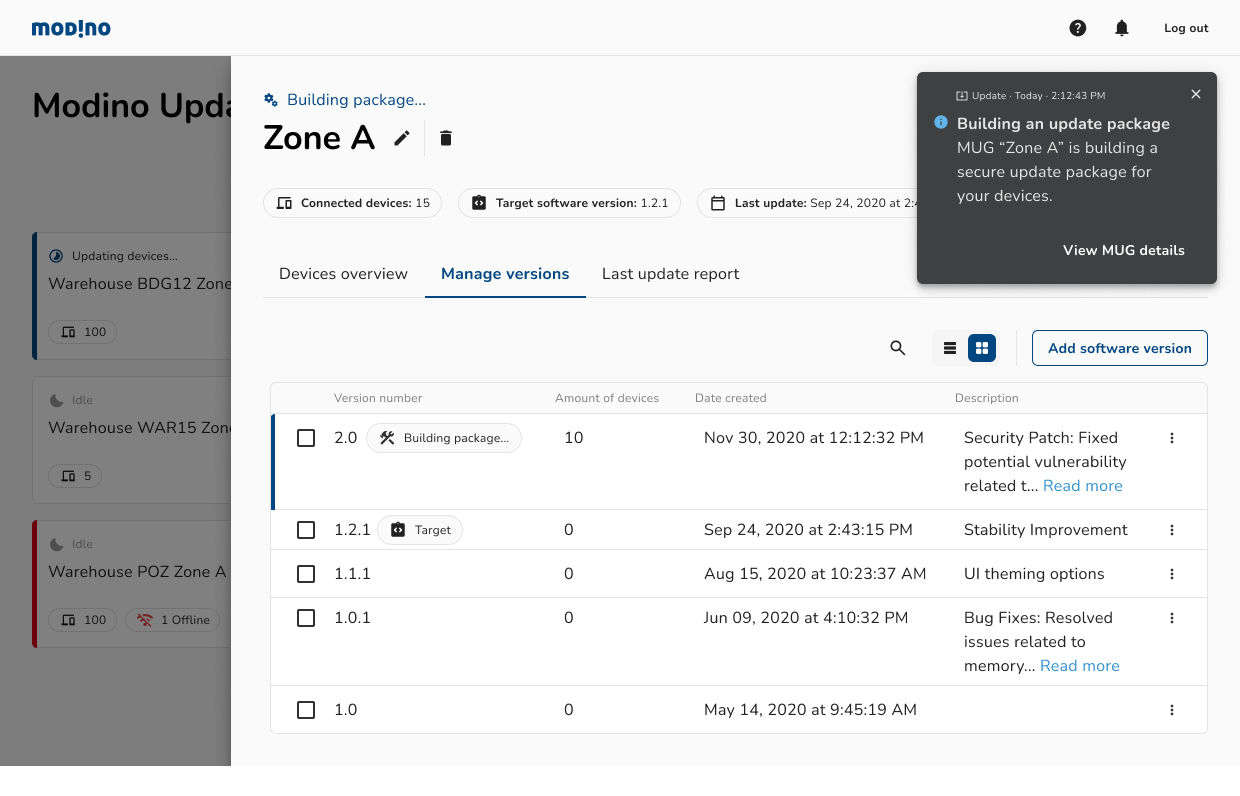
Modino.io - safe and secure digital artifacts delivery
Modino.io is an on-prem / cloud platform for performing safe and secure updates for: - IoT devices -...
PCert - re:align trust - PQC, CBOM, SBOM, inventory
Secfense User Access Security Broker (UASB) | Switch to MFA, FIDO2 or Passkeys in 5 minutes
The Secfense User Access Security Broker streamlines the adoption of multi-factor and FIDO2...
Trakia Cyber Range
Digital Innovation Hub Trakia builds and offers free-of-charge a Cyber Range as a Service solution...
Cyber Trust Label
The Cyber Trust Label shows that you are a secure and trustful organisation within the supply chain...